System API call hooking
I have for sometime been meaning to investigate into how exactly one set about hooking system API calls, i.e., be able to intercept/instrument calls to Win32 APIs made by any given process on the system. Surprisingly, there are quite a few good, informed articles on the subject. Here're some links to a few of them:
API hooking revealed
A good article that covers all the options available to achieve this.Process-wide API spying - an ultimate hack
Describes Import Address Table (IAT) patching in fair detail.Three Ways to Inject Your Code into Another Process
Another API spying DLL injection article.Windows NT System-Call Hooking
A great article from Mark Russinovich and Bryce Cogswell of Sysinternals fame detailing interception of system calls by patching system call dispatch tables from the kernel mode.Tracing NT Kernel-Mode Calls
Talks about intercepting kernel mode APIs such asIoAllocateIrpandIoCallDriver.My primary interest was in being able to intercept calls to APIs like
CopyFile,MoveFileandDeleteFile. Having recently developed an interest in kernel mode programming I initially figured that I'll write this as some sort of kernel mode filter driver and roll a super-cool interception system. But I came to realise in the end that this was not going to be possible without writing some fairly intricate and basically shaky code. As the articles I've given links to above indicate, it is quite possible to do this with a lot less fuss from user mode itself.
To avoid duplicating information already available in these articles I'll just briefly describe the approach I took:
- I created a DLL that would hook routines that I am interested in from
DllMain. - I would then inject this DLL into the process that I am interested in using the
CreateRemoteThreadtechnique. - The injected DLL would call back to the EXE whenever the relevant APIs were called by sending
WM_COPY_DATAmessages.
That's all! One thing that I did not do however is implementing the fancy IAT patching code myself. I used the Microsoft Research Detours library for doing this which does it in a very clean structured fashion. And finally, the whole thing will work only on systems running Windows 2000 and later (who uses Windows 95, 98 and ME anyway!).
Here's a screen shot of what the UI for this program that I wrote looks like:
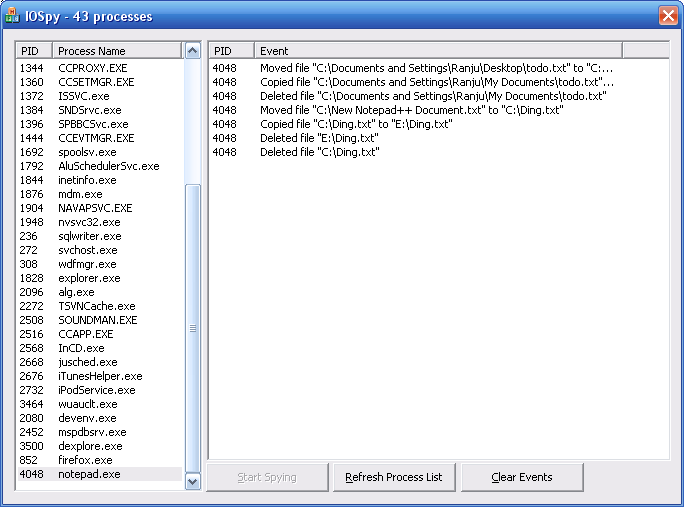
And here're the binaries and the source code should you feel like taking a look. Please note that I haven't included the Detours library here. You'll have to download it from the link given here yourself (it's only 519 KB in size) and set your build environment up so that the compiler and the linker can find the "detours.h", "detours.lib" and the "detoured.lib" files.